Azure Hierarchy
Overview
Azure's hierarchy is structured to organize resources, manage permissions, and control costs. Here is an overview of the main components in the Azure hierarchy:
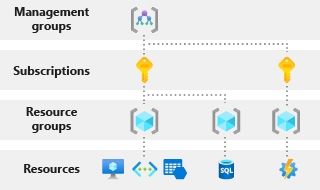
Hierarchy Resources
1. Tenant (Azure Active Directory)
Top-Level Identity and Directory Service: The tenant is linked to an instance of Azure Active Directory (Azure AD). It provides identity, access management, and directory services for users, groups, and applications.
Single Tenant per Organization: Typically, an organization will have a single tenant that spans across all its Azure services.
2. Management Groups
Organizational Containers: Management groups allow you to organize subscriptions into containers. You can apply governance policies and access control across multiple subscriptions.
3. Subscriptions
Billing and Access Control: Each subscription is linked to a billing account. Subscriptions provide a way to manage and isolate resources and access control. Billing and usage reporting are done at the subscription level.
4. Resource Groups
Logical Containers: Resource groups are logical containers for resources like virtual machines, databases, and storage accounts. All resources in a resource group should share the same lifecycle and management policies.
5. Resources
Individual Services: Resources are the actual services you deploy, such as virtual machines, web apps, databases, etc. Each resource is created within a resource group and a specific region.
Key Concepts
Tenant (Azure AD): Provides identity, access management, and directory services for the entire organization.
Management Groups: Useful for applying policies and RBAC (Role-Based Access Control) across multiple subscriptions.
Subscriptions: Act as boundaries for billing, resource management, and quotas. Each subscription has its own set of policies and RBAC settings.
Resource Groups: Logical grouping of related resources for easier management and lifecycle operations (like deployment, updating, and deleting).
Resources: The actual Azure services you use and manage.
Additional Concepts
Azure Active Directory (Azure AD): Centralized identity and access management service. It is used to control access to resources in Azure.
Policies: Used to enforce organizational standards and to assess compliance at various scopes: management groups, subscriptions, or resource groups.
Role-Based Access Control (RBAC): Provides fine-grained access management for Azure resources. Roles can be assigned at different levels (management group, subscription, resource group, or resource).
Organization Example
Suppose your organization is Fintech company and has multiple departments, each with its own set of applications and services:
Key Points:
Tenant (FinTech Inc): Represents the organization.
Root Management Group: The top-level management group.
Finance Management Group: Contains subscriptions and resource groups for the Finance department.
Finance-Prod, Finance-Dev, Finance-Test: Subscriptions for production, development, and testing environments within the Finance department.
IT Management Group: Contains subscriptions and resource groups for the IT department.
IT-Prod, IT-Dev, IT-Test: Subscriptions for production, development, and testing environments within the IT department.
Product Development Management Group: Contains subscriptions and resource groups for the product development teams.
ProdDev-Prod, ProdDev-Dev, ProdDev-Test: Subscriptions for production, development, and testing environments within the product development teams.
Central Services Management Group: Manages shared services and security resources across the organization.
Central-Shared, Central-Security: Subscriptions for shared services and security resources.
Resource Organization Documentation
Last updated